Schema - A schema defines the list of attributes that describe a given type of object. For example, let's say that all printer objects are defined by name, PDL type and speed attributes. This list of attributes comprises the schema for the object class "printers". The schema is customizable, meaning that the attributes that define an object class can be modified.
Attributes - An attribute describes an object. For example, passwords and names are attributes of user objects. Different objects will have a different set of attributes that define them, however, different objects may also share attributes. For example, a printer and Windows Vista computer may both have an IP address as an attribute.
Objects - Objects in the database can include printers, users, servers, clients, shares, services, etc. and are the most basic component of the directory.
Now that we have looked at the big picture, it is time to take a look at what happens inside a domain. To get started, the first concept that you will need to understand what the directory is made of. A common analogy for a directory is a phonebook. Both contain listings of various objects and information and properties about them. Within the directory are several other terms that you must know to gain even an entry level understanding as to how it all works.
These changes save an adminstrator some of the time consuming administration efforts spent creating and maintaining trusts. 1-way trusts can still be created when necessary.
Trusts are automatically transitive which means that if domain A trusts domain B and domain B trusts domain C, then domain A trusts domain C and vice versa.
Trusts are now commutative 2-way trusts. This means that if domain A trusts domain B then the reverse is automatically true. In Windows NT 4.0 trusts had to be administered as a series of 1 way trusts and could be quite cumbersome.
When a new domain is added, trust relationships are automatically configured.
Trusts are much more easily managed in Active Directory than they were in NT 4.0. There are 2 main reasons that this is the case.
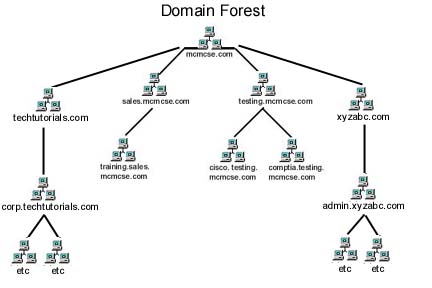
So let's say that our company owns techtutorials.net (actually that is true) and xyzabc. You can see that the individual trees are organized just like the root domain (mcmcse).
You can see that the structure begins to take the shape of a tree with branches and sub-branches. Now what if we are a company like Microsoft or DuPont that owns several other corporations. Typically, each company would have its own tree and these would be aggregated together via trusts to create a "forest". Let's look at an example using our site.
When a root domain and at least 1 child domain have been created, a "tree" is formed. Remember and understand this term as you will hear it often when working with a directory service.
Each domain controller in a domain is capable of accepting requests for changes to the domain database and replicating that information with the other DCs in the domain. The first domain that is created is referred to as the "root domain" and is at the top of the directory tree. All subsequent domains will live beneath the root domain and are referred to as child domains. The child domain names must be unique.
One thing that didn't changed from the NT 4.0 days is the use of domains. A domain is still the centerpiece of a Windows network, however, it is set up differently. Domain controllers are no longer separated into PDCs and BDCs. Now there are simply DCs (Domain Controllers). By default, servers are installed as Standalone Member Servers. DCPROMO.EXE is the Active Directory Installation Wizard and is used to promote a non-domain controller to a DC and vice versa. The wizard prompts for all of the required information to install Active Directory under the conditions that you have asked it to run Knowledge Consistency Checker (KCC) - This is a service created in order to ensure that the Active Directory service can replicate properly. It runs on all DCs and automatically establishes connections between individual computers in the same site. These are known as Active Directory connection objects. An administrator can establish additional connection objects or remove connection objects, but at any point where replication within a site becomes impossible or has a single point of failure, the KCC steps in and establishes as many new connection objects as necessary to resume Active Directory replication.
First let's introduce the concept of "Sites". Sites are used to define the boundaries of high-speed links on a network containing Active Directory Servers. Sites are based on IP subnets and are defined as a "well-connected subnet or subnets". Do not confuse this term with the concept of domains which are discussed next.
Active Directory is essentially a database of network resources (known as objects) and information about each of these objects. While NT 4.0 was a pretty good networking operating system back in the day, it wasn't entirely equipped for enterprise networking. The network neighborhood was a great tool until you had a huge network, then browsing problems would begin and finding a particular printer or server could become a nightmare especially if you didn't know the name of it. Furthermore, in order to even accomodate such a network, you would most likely have to partition it into several domains connected with trust relationships. AD solved many of these problems and offered a new level of scalability and orginization for enterprise computing. The directory of each domain can store as many as 10 million objects which is enough to accommodate millions of users per domain.
Introduction to Active Directory Architecture
We have a total of 90239 posts!
The best free certification study guides, practice tests and forums!
MC MCSE: Introduction to Active Directory Architecture
Комментариев нет:
Отправить комментарий